Sunday, December 9, 2007
back from the dead..
My theory is that they just adapted a "Prepaid service platform" so that time, they were'nt so familiar with that platform so they can't do much changes to it. Now that they're familiar with it, they were able to integrate prepaid sims with prepaid services.
I would'nt be surprised if some other services that vanished before will come back to life..
Wednesday, December 5, 2007
Choo choo
In school, we were always reminded that when creating programs, the target user should be able to understand it. We, as IT people most probably know how to go around with the programs that we made, but to other people, it may be hard and not "automatic". So training the users with your program will really help the company be more efficient.
From what i have noticed in my ojt, big companies really spend a lot on training, even if their people have high positions already, they are always put into training.
Sunday, December 2, 2007
Change
Sometimes, i want to create websites. but i always think, how will it be successful? I thought that i should create something that people are used to, and not make them used to something that i created
Tuesday, November 27, 2007
Project 5

There have been a lot of people saying that static can destroy computer hardware. The question is, is it true that a simple static discharge can destroy computer hardware or not? It is hard to believe that a discharge of electricity for just a fraction of a second can destroy our computer, but believe it or not, it really can destroy computer hardware.
Before we talk about how it can destroy our hardware, lets first talk about what friction really is. Friction really happens on the atomic level, when one thing is rubbed to another thing, transfer of electrons happen. I think the most common example of static friction is when you rub a balloon on your head, you will notice that when you lift the balloon, some of your hair rises with it, and you can also head some “sparkly” sounds while doing it.
If you look at the illustration above, you can see that same charges repel and opposites attract, this is what happens to your hair, the balloon has a different charge with your hair so when you pull the balloon away from your head, your hair is “attracted” to the balloon. The type of charge ( + or - ) transferred will depend on the type of materials that are rubbed together, for example, if a person walks on a carpeted room, that person can contain a charge from 10,000 volts to 12,000 volts (static electricity). The more electrons that have transferred during the rubbing, the higher the charge, and this charge can be discharged (make an electron flow) by sticking it into an opposite charge or simply a ground (neutral). And this is what happens when you touch the components of a computer, the computer usually is the ground, and you are the one charged. When you touch your computer, there will be a flow of electrons, which will give a shock of electricity to you and the computer.
Now, how can it destroy hardware? Computer parts are made from basic electronic components, a Dynamic RAM is made from capacitors, each bit is “memorized” by using a capacitor for each bit, so for example, for one clock cycle, the data to be saved to an 8 bit ram is 10010101, C1, C4, C6, and C8 will be charged by a voltage to represent a 1, and all other capacitors will be grounded so that it will have a charge of 0v and it will represent a 0. If you look at capacitors, they have ratings like 1pF 5v, this means that it has a capacity of 1 picofarad, and can hold up to 5v. If you go over that rating, that component can be damaged, imagine if 1 bit of your ram (1 capacitor) is damaged, if you want to save 1111111 in your ram, it may save 10111111 because of a damaged capacitor and imagine what that can do to your computers calculations. Also, processors, and other parts of your computer uses transistors for switching, these transistors, like any other electronic components have ratings too wherein it will only work properly within that range given, any other value used may result into the malfunction or damage of that component. Imagine if 1 transistor gets shorted because of over-voltage and fails to switch, surely, your computer will have errors in its computations. If you’re familiar with your computer’s power supply output voltages, you will notice that it has the outputs 12v, 5v, and 3.3v. The 12v output is used by motors inside your computer, motors inside your CD-ROM, hard disk, cooling fans etc. The 3.3v, and 5v outputs are used by logic circuits in your computer, meaning, the logic circuits containing gates, flip flops etc in your computer only uses voltages<=5, and surely the ones who designed and made the hardware of your computers used components that are near these voltages (economical reasons). Let’s say they have used components with ratings 3x as much as the ones required, Imagine shocking it with 10,000v, it is still a lot more, and it will surely cause damage to those components.
How can we prevent it? Although not all places have the potential to produce static, we should still do some precautions to avoid damage to computer hardware due to static. Here are some ways to prevent static,
· The simplest way is to touch, your computer’s casing before touching the hardware inside it. This kills the potential or it equalizes the difference of charges between you and the computer.
· Use computer grounding, I’m sure that you have noticed that computers have 3 prongs, 2 flat, and one round one. The round one is the ground, it has a neutral voltage, like what was said above, static electricity discharges to objects with an opposite, or a neutral charge. Just make sure that the ground in your socket is really connected.
· Use a wrist strap, this has the same principle with the grounding of the computer, but instead of the computer being grounded (neutralized), it is you who will be neutralized so that your charge will be killed.
Sources
http://www.skolnik-tech.com/esd.gif
http://everything2.com/index.pl?node_id=931175
http://www.webopedia.com/DidYouKnow/Computer_Science/2002/static.asp
http://www.pcworld.com/article/id,82184-page,1/article.html
http://www.sciencemadesimple.com/static.html
COMPARC Lectures
Project 4

Most of the people today have broadband connection in their homes, and one of the common things you need in order to share that connection to your computers at home is a router (or at least to simplify sharing your connection). I chose the WRT54G for Linksys and the WGR614 for Netgear because they have pretty much the same functions and features, and I am running the two at home so I could also put some of my experiences with these products in this paper. Both have a 4 port switch, 802.11b/g capability, and a WAN port. Before, I thought that every router that have the same features will be the same, but I soon learned that each router has its own ups and downs, lets talk about these routers’ ups and downs. It’s not just about the label & the features written on the box.
First, lets compare the prices of the two. The Linksys router costs P2860, while the Netgear Router costs P2290. The Netgear Router is P570 pesos cheaper than the Linksys router, does that mean that the Netgear Router is a better choice?
Second, the “User Friendliness” of the routers. Are they easy to set up? Or do you have to have advanced knowledge in networking for you to make it work? The Linksys Router comes with a CD which when inserted in your computer runs a Setup Wizard. This Wizard allows the users to setup their routers easily, they could fill up settings required by their ISP, clone the MAC address of that PC, change the name of the router, change the SSID or the name of your access point that will be broadcasted for wifi clients, etc. This wizard will surely make your router run properly in no time. The Netgear router on the other hand doesn’t come with a CD, but it runs a Setup Wizard when you access its control panel for the first time. Also, Netgear’s Setup Wizard shows pictures where you should plug in the wire from the modem, and the wires from the computers.
Now lets talk about the Routers’ Security. Linksys routers have a built in firewall to prevent attacks to be done to the router and its clients, MAC filtering to limit the connection to your network to known computers, Website blocking to allow or disallow access to certain sites, Keyword blocking to allow or disallow sites containing certain words. One good thing about the Linksys router’s security feature is that you can set the computers which you want to limit access to, but the website blocking and keyword blocking doesn’t work well. The Netgear router on the other hand also has MAC filtering, Website blocking and Keyword blocking, but the Website and keyword blocking unlike Linksys will apply to all computers which connect to your network, this can be a downside when you want to limit selected computers only. Netgear also has a security feature called Blocked Services, you can block selected ports no data will be sent or received using that port. Netgear also has an Email feature, you just have to set your POP/SMTP mail settings, and then it will send the log of incoming and outgoing requests, sites visited, and if there are violations made such as visiting blocked sites or sites with blocked words through email which is a great feature when you want to keep track of your network activity.
Now how about the routers’ wireless capabilities? First of all, both routers support 802.11 B and G, both have security features such as WEP, WPA, and WPA2, encryption like these are useful because you don’t want people to be “hopping” on to your network and accessing your files. Linksys has a feature wherein you can choose not to broadcast your SSID, this is useful when you want to hide your WLAN, Netgear doesn’t. Also, one of the most important factor when choosing wifi routers is the range.

The numbers above represent the effective range of 802.11 of the routers, and this statistic is true. If you look at the routers, you would think that the Linksys router would have a greater range because it has 2 big fat antennas, and the Netgear router just has a single antenna which is shorter than a pen. I have a Linksys router on the 3rd floor and a Netgear router on the 1st. The Linksys router wifi signal hardly reaches the rooms on the 2nd floor, and the Netgear router’s signal can reach the rooms in the 3rd floor, I can even use the wifi outside the house.
Lastly, what tweaks/upgrades can be done to the routers? We have seen before in past discussions that the “upgradability” of a hardware can help sell it. In the Netgear router, there can hardly be any tweaks done aside from the firmware upgrade wherein the router downloads it automatically from Netgear’s website, but with the Linksys router, there are tons of tweaks that can be done. First of all, Linksys sells high gain antennas which they claimed to improve signal strength but the antenna itself costs as much as a Netgear router. Some people also treat Linksys routers as real computers, they overclock it, and because Linksys routers run of Linux, they sometimes change the firmware of these routers using 3rd party firmware, and these firmware most of the time work better than the original firmware from Linksys.
So, which router is better? Well, it depends on who’s going to use it and what they’re going to use it for.
![]()
Sources
http://chriscarey.com/software/gkrellm/wrt54g/
http://www.netgear.com/Products/RoutersandGateways/GWirelessRouters/WGR614.aspx
http://reviews.cnet.com/routers/
NETGEAR Control Panel v7
Linksys Control Panel v7
http://www.batbox.org/wrt54g-linux.html
http://tldp.org/HOWTO/Linksys-Blue-Box-Router-HOWTO/
http://www.linuxdevices.com/news/NS4729641740.html
Project 2
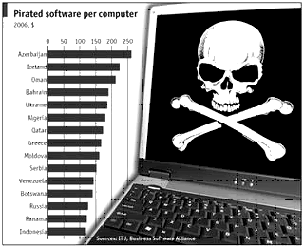
Software Piracy
Software piracy has been a problem in the
It is funny why the
If you look ath PAPT’s website, their main target are the users of pirated software and not the people who reproduce copies of those software mainly because they follow RA 8293. I think that it would really be helpful if an anti-piracy law was made so that not only the users but also the ones who reproduce copies of software can be arrested.
Why is software piracy bad? Companies have spent a lot of money in producing software, this is the reason why they have to sell it. If you buy pirated copies of software, the money goes to the pirates (for cost of reproducing), instead of the money going to the real creators/owners of the software (for cost of planning, designing, programming, analyzing, testing, etc). It is very similar to stealing, when buying pirated software, you have stolen the money that was supposed to be for them.
In the
When I bought a copy of Microsoft Office 97, I can still remember that it just cost about P6,000, it was still acceptable. When Office 2000 came out, I wanted to upgrade my Office so I went to the mall to buy a copy of it, I was surprised when I asked how much it was, it cost P16,000 pesos. I felt that it was too much, I mean it’s a good investment for businesses because they can use it and earn money, but P16,000 pesos for something to let you type your homework? That’s too much!
I have read something from “to pres GMA” forum. A guy wrote what he thinks of the governments move against software piracy. One of the things that he said was “Anti-Piracy Laws are laws that KISS THE BUTTOCKS of the foreign capitalists and lash the poor”. I wasn’t surprised, I also feel that our government doesn’t care about what the Filipino people thinks but they care more about what other countries think. Also he said that “The cost of legally buying a Windows XP program is in the amount even the upper class Filipinos cannot afford.” I strongly agree with his statement BUT the price isn’t a valid reason to be a pirate. There are some open source software that are free. These open source software can substitute for the expensive software, and sometimes, these open source software are even better that the expensive ones.
So why don’t people use those open source software? Based from my experience, I would want to use software created by a trusted brand/company. I wouldn’t want to try anything else but the one I have already known. The next reason is compatibility, the open source software may not be compatible with the “already known software”. Third reason is, maybe people are not aware that open source software exist. So I guess if people try and use these open source software (not only IT people but all), piracy will go down.
But this raises another question, how will people like us benefit if people will use open source and not buy from us? People can still buy software that we make, specially “custom made” software. I believe that most open source programs are general purpose, or software that are commonly used by a lot of people.
![]()
Sources
http://www.google.com.ph/search?hl=en&q=define%3A+software+piracy&btnG=Google+Search&
http://www.papt.org.ph/
http://www.papt.org.ph/uploads/file/RA8293%20IP%20Code.pdf
http://www.gov.ph/forum/thread.asp?rootID=68555&catID=2
http://reachupward.blogspot.com/2006/07/is-software-piracy-bad.html
Project 1
How did IBM sell their first PC’s? Why did it Click? 
Before reading about IBM’s first PC’s, I had a few guesses on why it could have “clicked” during that time. I said, maybe because they used to create calculators and typewriters before, maybe they have gotten the trust of the people, or maybe their computers are cheaper.
During that time, there were other companies who developed their own PC’s. My first guess may be a factor, but not exactly the reason why they were able to sell. My second guess was proven false after reading some articles about the IBM 5100.
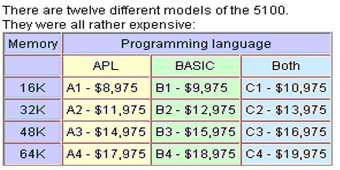
( figures from http://oldcomputers.net/ibm5100.html )
If you want to buy an IBM 5100, you should at least have $8,975. I think that that’s too much for a small object that looks like a typewriter. The 5150 was a lot cheaper, it was sold for about $3000, but still expensive. If you take a look at the price of the C4 model, that could already buy you a car. So I guess the price wasn’t the reason of their success.
While reading some articles about the first IBM PC’s (5100 and 5150), I have read some advantages it had over its competitors. IBM PC’s during their time was not the most powerful PC, but it had a feature that no other PC had. It gave the owners/users the ability to “upgrade” their PC’s or in other words it was expandable. There were expansion slots on the main board that allowed users to add memory modules, connect serial and/or parallel peripherals, etc. I think that IBM’s idea was brilliant. If they had not done this, and a component of a PC dies out, you can consider your PC as junk. Also, I think that everyone wants to get something that they can customize, people like customizing things, from cars, to cellphones, even computers.
IBM also implemented the “open architecture”. They sold the “IBM PC Technical Reference Manual” which some source codes written on the computers ROM, also I think that the manual contained the Op Codes (for low level programming) so that other developers may create hardware and software that can be used for IBM PC’s. I think that what they did was something that the other computer companies have thought of also, but have thought of as a downfall. Because if you show your design to others, they might just copy it and steal it from you, but IBM did it, and it became a factor of their success.
One last thing that I think lead to the success of IBM is the fact that their computers were highly available. There were more than 190 stores of Computerland that already existed when IBM released the PC’s which lead to the immediate widespread distribution of IBM’s computers.
I believe that IBM had a great influence on how computers, computer hardware, and software are made nowadays. First of all, modern computers allow the owners/users to customize them, they could add memory, add PCI devices, add a video card and more, they could even change the processor. For me, a computer that allows upgrades or its parts to be replaced are the real General Purpose Computers because if you can add devices to your computer, you could do virtually anything, it is just limited by the number of sockets or ports on your motherboard. I still remember my first laptop, it was a Pentium I 133 (about 10 years ago) whenever I see new technology on the television or in the magazines, I would feel bad because I couldn’t get that for my laptop. I was limited to what my laptop had originally. Nowadays, it’s already possible, there are laptops which allows you to add devices internally (like PCI devices but the laptop version), and I think that this became available because they saw that this is what the people need like what IBM anticipated before.
Nowadays, open-source programs can be found almost anywhere. One of the most popular open source programs is Linux. Look at how great it is now, it is because of the efforts of a lot of people sharing their ideas on how to improve the OS more. I think that IBM made the right move by opening their source code to the public (at least the contents of the BIOS). I think that their intention was to allow the programmers to study how their machine works in order for them to create programs for that machine, but maybe during their time, when they released their source codes, other programmers may have found bugs and reported those bugs to them which may have improved the software of IBM’s PC’s.
![]()
Sources
· http://en.wikipedia.org/wiki/IBM_PC
· http://oldcomputers.net/
· http://www.pseriestech.org/gallery/data/501/historyofibm.gif
Project 3


Watching TV series isn’t my thing. I can’t believe that I didn’t fall asleep while watching this. Maybe it was because we were allowed to critique the parts in the video that were related with computers. It is funny seeing how some video makers exaggerate what technology can do (in that time).
There are some parts of the video which I found interesting. First of which is the part when they have already have the victim’s laptop and they were trying to view the contents of that laptop. First of all, the video was made on 2002, operating systems already implemented “User Logins”. Computer users are required to give a password in order to use the computer, unless it was set to none, but if they said that the computer contained important information, why wouldn’t the owner put a password? Assuming that the owner set a password, it would be hard for them to guess that password or even crack it because they only would have 1 input box for the password and no place where they can type in commands for them to crack in the system. It may still be possible if they have tried several passwords (brute force).
When they opened the laptop and looked at the files, they found that a file was accessed after the victim was killed. For me, the file access timestamp is not that reliable because you can “cheat” it. You can do this by changing the system time and date, then that date and time will be the one used by the system for the timestamp.
The next thing that I found interesting was when the IT girl said that passwords can be easily cracked. My first reaction was, I don’t think so. Not all passwords can be cracked easily, that’s why encryption, and hashing were made so that hackers can’t read passwords in plain text. But if she was referring to the password protection of files like Microsoft Office Documents (*.doc), yes it can be easily cracked, there are a lot of software out there that does this for you and I have tried a couple of them.
It was also mentioned in the movie that deleted files can be retrieved. This thing is true, files are a linked list, and we know how a linked list works. When a file is deleted, the address of the head of the file deleted is forgotten so that the file will be “lost”. If you’ll be able to find the head, you’ll be able to access the deleted file, that is, if the user of the computer isn’t fond of saving big amounts of data all the time which may have overwritten parts of “lost/deleted” files. But this can be said false if the user of the computer used a file shredder.
Another interesting part was when the IT expert discussed how the bad guy knew what the victim was doing in her computer. The IT expert mentioned that it was because of a worm that she opened from her email. At first, I felt that this idea was preposterous because I haven’t encountered a virus that bad, not even something close to that, and second, if that kind of virus was made, and it spread to billions of computers, imagine how much computers the hackers would be able to watch, but for what? I bet that a big percentage of the ones that they can access wont give helpful information. But if the virus was made specifically for her, it can be possible. There are a lot of programs wherein you can watch/control remote computers like VNC and NetOP, if a program can do it, why not a virus? A virus is still a program.
Next thing that they mentioned was, there were not much laws that they can use against the bad guy. I believe that this is true, specially here in the
Another thing that they said was they could trace email through the header of the email. This is something that is true, when you read the header of emails, you will see there the IP address of the sender, IP of the recipient, and also the servers & routers where the email passed in order to get from the source to the destination. This thing can still be cheated IF a machine was programmed to do so, whenever a hop is made, that machine adds its identity in the header, that machine if maliciously programmed, can change everything in the header so that it will be impossible to trace the source, but things like these can be easily detected because of discrepancies in the “hops”, time, etc.
It was also mentioned that a deleted email can still be read, I think that it depends on how the system is implemented. If it was really deleted from the disk (cut the link to the head of file), there is a high chance that the email may have been overwritten specially if that server has a lot of users (incoming of mail may have overwritten the deleted mail) but there is still a chance that the mail is still preserved in the disk. But if she was referring to Delete and send to Trash, of course it can be easily found.
Lastly, a company that steals information. When they showed the office of that company, I didn’t believe it at all. First of all, before you can put up a company, the government should approve it, do you think that the government would allow something like that? I think that a lot of underground things like this happens but not like how they showed it in the video. Also, I believe that the
All in all, I think that that episode was well thought of.
Wednesday, November 21, 2007
Piracy ulit..
- broken bit
- physical hardware
- online activation
how can this be cheated?
-broken bit, if a copying machine was used (not pc+nero but bit by bit copying) of course that broken bit will be copied because that machine doesnt care if that is an error unlike a computer that will stop copying because it sees an error
-physical hardware, if you know what's needed to be sent by that hardware, you can make it yourself, i bet it's still cheaper
-online activation, point their servers address to a server that you setup(f you know the data being sent by their servers to activate your software)
but i remembered the ps2.. i asked sir jade pabico how sony's anti piracy works, because even if you copy the cd bit by bit, it still doesnt work, he said that it might be the cd/dvd's serial number, sony may have had reserved a range of serial numbers, and then if the ps2 reads that the cd/dvd is within that range, then it should run..
i just dont know if you can cheat that serial number
Wednesday, November 14, 2007
Licensed software..
Windows 98
Genuine License
For distribution with a new pc
I just laughed, i wanted to look at the other cash registers if they had the same photocopied license but people might think i'm weird if i go from one cash register to another and look at that laminated paper.
by seeing that, i just realized that big establishments are really the target of the "anti-piracy team"..or else they wouldnt have placed that in their counters.. but a photocopied license? would that make them more questionable rather than not exposing the license unless when they were asked?
Sunday, November 4, 2007
Spam? or Not?
From: encarnacionadlsc
Sent: Tuesday, October 23, 2007 2:37am
To: ManTech-07-08-2@yahoogroups.com
Subject: [ManTech-07-08-2] Is this spam or not?
Below is an actual email I received this Monday. The question is, is
it spam or not? It is one of the things we'll discuss next lecture.
Don't forget to post on your blogs from last lecture.
P.S. I suggest you don't reply to the email below.
From: "lehcir_21" <lehcir_21@yahoo.
Add Mobile Alert
To: "testwynnewynne" <testing@ph.mensa.
Subject: call center vacancy
Date: Mon, 22 Oct 2007 16:49:49 +0800
Call center operator
JHC Inc is looking for intelligent people for this position ready
for a
career growth and hardworking.
Requirements:
- FULL TIME JOB ONLY
- Computer with broadband Internet access (Ability to be online
frequently ).
- Adult people only! (21 plus).
- Solid communication skills.
- Aggressive and insensitive persuasion skills must be as an
advantage
- Working experience in HR management and Call center area are
greeted
Salary:
$200/week
Annual bonuses
Please direct your resumes to blefeb4128aw@
SPAM! Well, my blog isnt about that email. I wanted to talk about an experience of mine with this spam sh*t. I maintain a website with its own mail server, I was paying for that server to run so i had the right to use it by myself (or at least the one with my name). One time, i just got surprised that all the emails that i would send to people using yahoo mail, would go to their spam folder. I soon found out that my mail server wasnt set to require a valid username & password in order to send an email, meaning anyone who accesses it can send an email with the address of the server on it. So i reported it to yahoo and my hosting and they fixed it right away.
DO NOT TRY THIS AT HOME!
one time, nangtrip lang ako sa isang kaibigan. using php's mail function, you can send an email. and by changing the parameters that you put in that function, the contents of the mail will change, including the "sender". So i used my friends email as the "sender" and sent an email to his email, he thought that i got in his mailbox. I just wanted to point out that an email can be spoofed, even if you know that email, it doesnt necessarily mean that it really came from that person/server.. one thing that you can do is to look at the header and check the first hop, then ex, sender:email@yahoo.com, get the ip address of yahoo.com's mail server and compare it to the address of the computer in the first hop..but of course you dont have to do this everytime..I am not "yahoo.com" but i was able to send an email with "email@yahoo.com" using my server..
Wednesday, October 24, 2007
Just a thought on hashing..
I believe that hashing is really one way..because of the algorithm that it uses, but there is one thing that can "cheat" that. Lets say a password is from 6-10 characters long, so create a script that hashes and saved all possible combinations from 6 characters - 10 characters in a table
ex
Table hashtable
normal hashed(SHA1)
000001 0a620481ca00b00de7eedb407a68b9163dcabae3
000002 86dfb043360b0e9ef7767e6ea7ad09fb7fb81537
... ...
... ...
... ...
d3nn1s 7b7edb6fda80187ac8a3f18b2c2b9bfef7a95acc
... ...
ZZZZZZZZZX 3ae4c15d5da68511a49a6171d0df2f7e51207fa6
ZZZZZZZZZY 27fb26c695b91422e048b7ccd2557209472d7fbc
ZZZZZZZZZZ 5df31df13a3fe267e1ae0a35f71bdc70b0249d35
and if your script saved all these in a table, just search for example..
SELECT normal
FROM hashtable
WHERE hashed="7b7edb6fda80187ac8a3f18b2c2b9bfef7a95acc";
by that, you will surely get the reverse of that hashed word..which is d3nn1s, also, hash functions have a fixed length
MD4 = 32 characters
SHA1 = 40 characters
so it gives you a big clue on what hash function was used..unless if you do character stuffing..
and it is also a proof that hasing is one way (before the brute force), for example you hash this string using SHA1 "ang mantech na subject ay napakasayasayasayasayasaya talaga!", the result would be "5df31df13a3fe267e1ae0a35f71bdc70b0249d35", obviously, the string that you used is longer than 40 characters, and the end result is only 40 characters, so how can you derive a combination of 60 characters from 40 characters..it can only be done by "brute force" (hashtable)
Sunday, October 7, 2007
Attack!
I have heard of SQL injection before but I didn't know how much things an attacker can do using SQL injection. For me, there are many ways on how to prevent this, or at least minimize the damage (if ever an attack happens).
- the most basic thing to do is to create a separate user with limited privileges which the web application will use (only the privileges that the application will need, no more) so that if an attack like DROP TABLES is used, the command wont work, unless a drop privilege is given to that user.
- Second, to avoid getting information about/from your database from a public page, don't put a code that would print information that your database server returns, because if you do that, and an attacker discovers that he/she can inject an sql code, that page would be like a sql client for him/her.
- This I think is the safest but i think is not practical (last resort), when getting information from forms, encrypt it before connecting it to the sql code, because if you put a textbox on a page and will directly use the string that will be typed in the text box and will put that in your sql code, a hacker can easily inject a code. Surely, when the information from a form is encrypted before inserting that into the code, an attack would be almost impossible but it is impractical because when you view the contents of the database, it will all be encrypted.
Lastly, the thing that the guy from microsoft discussed about the attack on IIS, I think that this is really a problem when running a web server on winows. You can easily access files even from other folders by using "../", so if you use the "../" and know the folders of that server, you can traverse the folders of that server and steal some files. I think that this is not applicable in linux, in linux, you can set the permissions of folders. So if you plan to run your own web server, use linux :)
Wednesday, October 3, 2007
Taking advantage..
It is like leaving a 500 peso bill on the ground, surely someone see it and someone would pick that up. Same with these softwares, if you leave a hole open, in time, people will discover these holes and someone would also create something that can take advantage of that hole... So.. if in time, it will be discovered, I believe that viruses are just one of the ways to speed up the discovery of the bug, and is a great reason why they should fix it right away, thanks to the people who make them.
I think that it is one of the responsibilities of computer users to protect themselves from these viruses.
Sunday, September 30, 2007
How much will you charge?
Okay, back to pricing. About a couple of months ago, a friend of mine asked me if I could create a website for their school. They said they'll be in charged of hosting and domain, they just needed the design and the pages, and they will give me a list of things to put in the site. I have done a few websites before but for free so I didn't have any idea how much I'll charge them for this website. I was thinking of charging them 2-3 thousand for the design and pages because I felt that it was really simple. I got surprised that they offered to pay me 9 thousand for a simple website.
When you think about pricing, these are the things that I think you should consider.
- Intensity of work - how hard will that project be?
- Materials used - will you buy software/hardware for that project?
and these are additional things you may want to consider..
- Your/company's name - pag sikat, mas mahal. I think it's a pride thing. When you're known to do something great, you wouldn't want to keep your prices low because you'll look "cheap".
- You clients name - Like the school that asked me to do the website, It's a small school, but a school that has a lot of money. (i guess, dahil conio ang mga estudyante doon, mga foreigners eh hehe)
I believe that there are a lot more factors for pricing, but I think that these factors are one of the basic things to consider when you're estimating the price for a proposal.
Wednesday, September 26, 2007
Memories...
This is an external zip drive, I couldn't find the disk anymore, it looks like a normal diskette, it's a little bit thicker and the metal cover that opens is smaller.
Who thought that parallel ports (printer) can't be used for drives?
What's inside it? The insides look like the insides of a floppy drive.
If you look at the head, It is also magnetic, not optical.
We got this external zip drive, because when we bought a PC before that was bundled with an internal zip drive, but it was useless because we couldn't use the zip disk it to transfer files from that PC to another PC (hindi pa uso network dati pero may internet na mabagal). I think that this is one of the reasons why ZIP and JAZ failed.
I was thinking of a reason why some memories/disks that come out of the market succeed and some fail (in terms of sales & users).
Lets look at some examples of the disks/memories that became successful. CD writers came long after CD players and VCD players came out. DVD writers came out after a lot of people had DVD players in their homes. USB flash disks came out when computers already had USB ports and a lot of USB peripherals were already being used.
I felt that if manufacturers create a product that uses something that everyone already has instead of creating their own "trend", it has a great chance of being successful just like what I mentioned above.
So this puts another question in my head..Blue ray isn't that popular yet. Most of the people, I think, do not have blue ray players at home, and they are already introducing blue ray writers, and disks in the market.. will blue ray be successful? only time will tell..
Sunday, September 23, 2007
Mantech 3rd Blog
This story reminded me of our research about IBM, we really should take into consideration the availability of parts when we buy a PC (used or brand new), because if you wont be able to buy upgrades for your pc, you just wouldnt be able to catch up with the requirements of the programs that are released in the market and your pc, in time, will just end up as junk.
Thursday, September 20, 2007
Second Blog
If Charles Babbage had finished the Analytical Engine.....
I believe that the computers now would really a lot more advanced.

But there's one thing that amazes me. If you look at the Analytical Engine, it is mostly (if not all) mechanical. Who could ever think that by turning some wheels, you can yeild some answers.
There are some things in the Analytical Engine that I think can be related to the parts of a modern computer.
- First, the rod where the wheels are connected (bottom of the machine), i think that in the computers now, this is the clock. The faster this wheel turns the faster the computer can process data, also all the wheels are attached to it, it keeps the parts synchronized.
- The wheels on that rod, I think that the wheels on that rod has some grooves so that when it turns, it can "compute" for the answer or it can be conditions to either change the positions of the flat metal parts on the top, so i think that in modern computers, this is the ALU or the arithmetic logic unit which contains the basic operations and some conditions.
- and the last thing i could see that can be related to a modern computer are the flat metal sticks, notice on the left part of the engine, some of those flat metal parts are either pushed or pulled by the wheels, i think that this holds the data, so i can say that in modern computers, this is the flip flops, each metal part can hold 1 bit of data
This is mechanical, modern computers are purely electronic, how did this help in developing modern computers? First of all, i think that if Charles Babbage had created a machine that Automates jobs, it just proved that it can be done. Second, when we solve a problem, it is easy for us to solve something because we understand what the problem means, but a computer doesnt understand that, so he represented the data (numbers) into something that can be manipulated by a machine in order to come up with an answer.
I know that the older computers (older than analytical engine) like the abacus had a way to represent data (used balls to represent numbers), but in order to get an answer, someone should move the balls to get an answer, Charles Babbage was able to make that automated.
First Blog
Before I couldnt agree that the ABACUS was the first computer. Why? because first of all it looks a lot different from the computer we all know, second it's not electronic. I couldnt see a connection.

But when I was about to write this blog, I just saw a connection. I have seen how it could have influenced the design of modern computers.
I dont know how to use an abacus, but i know one thing, you either move the balls to the left or to the right. There's no such thing as putting the ball hanging in the middle.
The CPU's of modern computers are digital, they only understand 1's (highs) and 0's (lows). so i thought, that the abacus CAN be like the computer's CPU. if you place the balls on the left side, you may represent it with a low, and if you put the balls on the right you may represent it with a high..get the idea?
the only difference is..when you read high's and low's in a computer, you read it as binary (sign and magnitude, 2's complement, 1's complement depending on what was defined by the architecture). in an abacus, i think you count the balls, but the basic idea is the same, you represent the numbers (problem) using bits, then solve that problem using those bits, and then output the bits, then convert those bits (output/answer) to a number understandable by humans
Thats why i believe now that the abacus was the first computer..
